Mainframe Security:
The Future Is Here
Part 1
By Reg Harbeck
The PASSWORD data set has long since been superseded by the three External Security Managers (ESMs) available on IBM Z: IBM RACF (Resource Access Control Facility), Broadcom ACF2 (Access Control Facility 2) and TSS (Top Secret Security). They are each foundational to the world-leading securability of IBM Z, providing authentication, resource authorization, granular administrative authority and scoping, detailed logging, complete recovery, and many other features that stand in a class apart from what is available on any other computing platform.
Each of these ESMs have used encryption for more and more purposes over the years, beginning with encrypting passwords and then entire security databases. They have also been used to generate and manage public/private key pairs and interact with other aspects of encryption on the mainframe.
But mainframe security, and all types of computing security relevant to the mainframe, now exceed the scope of ESMs, so additional tools, both on and off the mainframe, have been introduced to continue to advance the securability of this key platform.
AI, Regulations and the Future
SPONSORED CONTENT

Reduce Your IT Risk & Build Customer Trust
Today’s IT risk landscape is ever-expanding. Reducing risk across organizations must be prioritized and IT risk management strategies constantly evaluated to keep pace with emerging threats while strengthening customer, partner, and investor trust.
You can bolster your IT risk management by choosing the right mainframe security solutions; implementing comprehensive cybersecurity measures; and prioritizing Zero Trust across your business. And Broadcom Mainframe Software is poised to partner with you every step of the way.
Here are some resources to get started:
- IT Risk Management
- Continuous Monitoring and Compliance
- Zero Trust and Identity
Multi-Factor Authentication
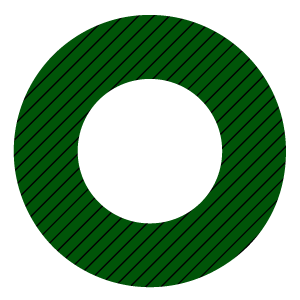


Multi-Factor Authentication (MFA) uses not just a user ID and password to log on (authenticate) to the mainframe, but also an additional separate factor, often accessed via a user’s mobile phone, though many other options exist.
As Ravi Patil, director of cybersecurity and compliance at Broadcom Mainframe Software, points out, “Research has been done to show that MFA is 99% effective in thwarting cyber attacks.” In other words, one of the most important ways to secure access to the mainframe is with the addition of something off the mainframe.
Encryption
As hinted earlier, encryption also exists well beyond the traditional purview of the ESMs. One key aspect of this is pervasive encryption–the ability for critical data on the IBM Z mainframe to be encrypted and decrypted as needed by the platform, so applications don’t need to be modified to benefit from it. Of course, everything has a trade-off in terms of resource usage, complexity and even relevance, so even though encryption is now broadly and readily available on IBM Z, it’s important to choose which things to encrypt.
Anne Dames, Distinguished Engineer at IBM, makes this clear. “One of the things that we think about when we are considering what data is it important to encrypt, we think about the sensitivity of that data. We think about whether or not that data needs to be kept secure for a short time or for a long time.
“So, the kind of information that you want to keep secure are things like personally identifiable information. You want to keep secure health records? You want to keep secure IP (intellectual property). You want to keep secure information that is considered sensitive. So those are some of the kinds of things that you might be storing in a data set that you might want to keep secure. You want to keep secure communication between two parties. So you want to make sure that it also is using algorithms that are secure.”
Quantum Computing
Ravi Patil answers crucial questions:

↪

↪




